AWS VPC Basics (AWS Series - Post 2)
Thu Apr 28 20228 min read
VPC Basics
When you create a VPC, you must specify a range of IPv4 addresses for the VPC in the form of a Classless Inter-Domain Routing (CIDR) block. For example, 10.0.0.0/16.
A VPC spans all of the Availability Zones in the Region. The following diagram shows a new VPC. After you create a VPC, you can add one or more subnets in each Availability Zone.
VPC Sizing
- Amazon VPC supports IPv4 and IPv6 addressing.
- A VPC must have an IPv4 CIDR block.
- You can optionally associate an IPv6 CIDR block with your VPC.
VPC Sizing for IPv4
- When you create a VPC, you must specify an IPv4 CIDR block for the VPC.
- The allowed block size is between a /16 net-mask (65,536 IP addresses) and /28 net-mask (16 IP addresses).
- After you’ve created your VPC, you can associate secondary CIDR blocks with the VPC.
It is recommended to specify a CIDR block from the private IPv4 address ranges
- 10.0.0.0 - 10.255.255.255 (10/8 prefix)
- 172.16.0.0 - 172.31.255.255 (172.16/12 prefix)
- 192.168.0.0 - 192.168.255.255 (192.168/16 prefix)
You can create a VPC with a publicly routable CIDR block that falls outside of the private IPv4 address ranges. But instances created in the VPC will NOT be publicly routable.
You can associate secondary IPv4 CIDR blocks with your VPC. When you associate a CIDR block with your VPC, a route is automatically added to your VPC route tables to enable routing within the VPC (the destination is the CIDR block and the target is local).
VPC CIDR Block Restrictions
To add a CIDR block to your VPC, the following rules apply:
- The allowed block size is between a /28 net-mask and /16 net-mask.
- The CIDR block must not overlap with any existing CIDR block that’s associated with the VPC.
- You cannot increase or decrease the size of an existing CIDR block.
- You have a quota on the number of CIDR blocks you can associate with a VPC and the number of routes you can add to a route table. You cannot associate a CIDR block if this results in you exceeding your quotas.
- The CIDR block must not be the same or larger than a destination CIDR range in a route in any of the VPC route tables. For example, in a VPC where the primary CIDR block is 10.2.0.0/16, you have an existing route in a route table with a destination of 10.0.0.0/24 to a virtual private gateway. You want to associate a secondary CIDR block in the 10.0.0.0/16 range. Because of the existing route, you cannot associate a CIDR block of 10.0.0.0/24 or larger. However, you can associate a secondary CIDR block of 10.0.0.0/25 or smaller.
- You can disassociate a CIDR block that you’ve associated with your VPC; however, you cannot disassociate the CIDR block with which you originally created the VPC (the primary CIDR block).
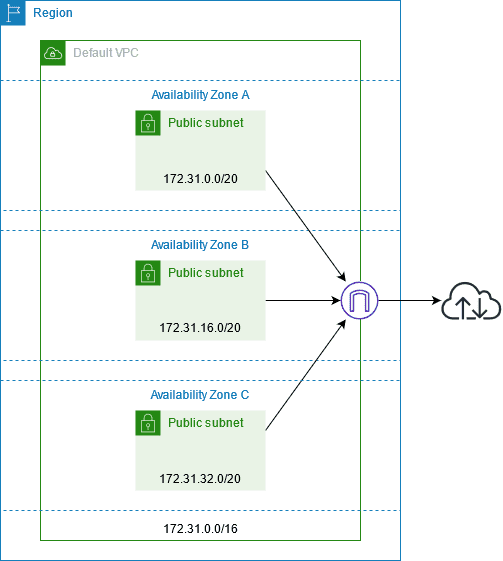
Default VPCs
When you start using Amazon VPC, you have a default VPC in each AWS Region. A default VPC comes with a public subnet in each Availability Zone, an internet gateway, and settings to enable DNS resolution.
A default VPC is suitable for getting started quickly and for launching public instances such as a blog or simple website. You can modify the components of your default VPC as needed. You can add subnets to your default VPC.
Default VPC components
When we create a default VPC, we do the following to set it up for you:
- A VPC with a size /16 IPv4 CIDR block (172.31.0.0/16). This provides up to 65,536 private IPv4 addresses.
- A size /20 default subnet in each Availability Zone. This provides up to 4,096 addresses per subnet, a few of which are reserved for our use.
- An internet gateway and connected to your default VPC.
- Add a route to the main route table that points all traffic (0.0.0.0/0) to the internet gateway.
- A default security group and associate it with your default VPC.
- A default network access control list (ACL) and associate it with your default VPC.
- Associate the default DHCP options set for your AWS account with your default VPC.
The following table shows the routes in the main route table for the default VPC.
| Destination | Target |
|---|---|
| 172.31.0.0/16 | local |
| 0.0.0.0/0 | internetgatewayid |
Default subnets
- By default, a default subnet is a public subnet, because the main route table sends the subnet’s traffic that is destined for the internet to the internet gateway.
- You can make a default subnet into a private subnet by removing the route from the destination 0.0.0.0/0 to the internet gateway. If you do this, no EC2 instance running in that subnet can access the internet.
- Instances that you launch into a default subnet receive both a public IPv4 address and a private IPv4 address, and both public and private DNS hostnames.
- Instances that you launch into a non-default subnet in a default VPC don’t receive a public IPv4 address or a DNS hostname.
- You can change your subnet’s default public IP addressing behavior.
VPC DNS Attributes
Domain Name System (DNS) is a standard by which names used on the internet are resolved to their corresponding IP addresses. A DNS hostname is a name that uniquely and absolutely names a computer; it’s composed of a host name and a domain name. DNS servers resolve DNS hostnames to their corresponding IP addresses.
Public IPv4 addresses enable communication over the internet, while private IPv4 addresses enable communication within the network of the instance.
Amazon DNS server
The Amazon DNS server is an Amazon Route 53 Resolver server. This server enables DNS for instances that need to communicate over the VPC’s internet gateway.
The Amazon DNS server does not reside within a specific subnet or Availability Zone in a VPC. It’s located at the address 169.254.169.253 (and the reserved IP address at the base of the VPC IPv4 network range, plus two) and fd00:ec2::253. For example, the Amazon DNS Server on a 10.0.0.0/16 network is located at 10.0.0.2.
When an instance is launched in a VPC -
- The instance is provided with a private DNS hostname
- A public DNS hostname if the instance is configured with a public IPv4 address and the VPC DNS attributes are enabled
- The Amazon DNS server in your VPC is used to resolve the DNS domain names that you specify in a private hosted zone in Route 53
DNS Hostnames
When an instance is launched in the VPC, it always receives a private IPv4 address and a private DNS hostname that corresponds to its private IPv4 address. If your instance has a public IPv4 address, the DNS attributes for its VPC determines whether it receives a public DNS hostname that corresponds to the public IPv4 address.
Private IP DNS name (IPv4 only)
- Can use the Private IP DNS name (IPv4 only) hostname for communication between instances in the same VPC
- Can resolve the Private IP DNS name (IPv4 only) hostnames of other instances in other VPCs as long as the instances are in the same AWS Region and the hostname of the other instance is in the private address space range
Public IPv4 DNS
- A public (external) IPv4 DNS hostname takes the form ec2-public-ipv4-address.compute-1.amazonaws.com for the us-east-1 Region
- For other regions it takes the form ec2-public-ipv4-address.region.compute.amazonaws.com
- The Amazon DNS server resolves a public DNS hostname to the public IPv4 address of the instance outside the network of the instance
- The Amazon DNS server resolves as private IPv4 address of the instance from within the network of the instance
DNS attributes in your VPC
The following attributes determine whether an instance launched into the VPC receives a public DNS hostname if it is assigned a public IPv4 address or an Elastic IP address at creation.
enableDnsHostnames
- Determines whether the VPC supports assigning public DNS hostnames to instances with public IP addresses.
- If both DNS attributes are true, instances in the VPC get public DNS hostnames.
- The default for this attribute is false unless the VPC is a default VPC or the VPC was created using the VPC console wizard.
enableDnsSupport
- Determines whether the VPC supports DNS resolution through the Amazon provided DNS server.
- If this attribute is true, queries to the Amazon provided DNS server succeed.
- The default for this attribute is true, no matter how the VPC is created.
Rule for DNS Attributes
Both are true
- Instances with public IP addresses receive corresponding public DNS hostnames.
- The Amazon Route 53 Resolver server can resolve Amazon-provided private DNS hostnames.
If at least one of them is false
- Instances with public IP addresses do not receive corresponding public DNS hostnames.
- The Amazon Route 53 Resolver cannot resolve Amazon-provided private DNS hostnames.
- Instances receive custom private DNS hostnames if there is a custom domain name in the DHCP options set.
Private hosted zones
- To access the resources in your VPC using custom DNS domain names, such as example.com, instead of using private IPv4 addresses or AWS-provided private DNS hostnames, you can create a private hosted zone in Route 53.
- A private hosted zone is a container that holds information about how you want to route traffic for a domain and its subdomains within one or more VPCs without exposing your resources to the internet.
- You can then create Route 53 resource record sets, which determine how Route 53 responds to queries for your domain and subdomains.
- To access resources using custom DNS domain names, you must be connected to an instance within your VPC.
I hope with this post, the basic components of AWS VPC is bit clearer. We will delve into more details in coming post.
Till then, happy coding !!!